SOAR Workflow Automation
Dreamer People's emphasizes SOAR (Security Orchestration, Automation, and Response) Workflow Automation in a Cyber Security Fusion Center (CFC). The primary goal is to minimize the risk of threat exposure and significantly expedite threat mitigation, achieving 30% – 95% increase in speed compared to manual methods.
We provide readily available playbooks designed to streamline the deployment of automation within the CFC without the need to start from scratch in identifying potential use cases, API integrations, workflows, and enrichment processes. In essence, Dreamer People offers a pre-packaged solution to enhance efficiency and effectiveness in responding to and mitigating cybersecurity threats within a CFC environment.
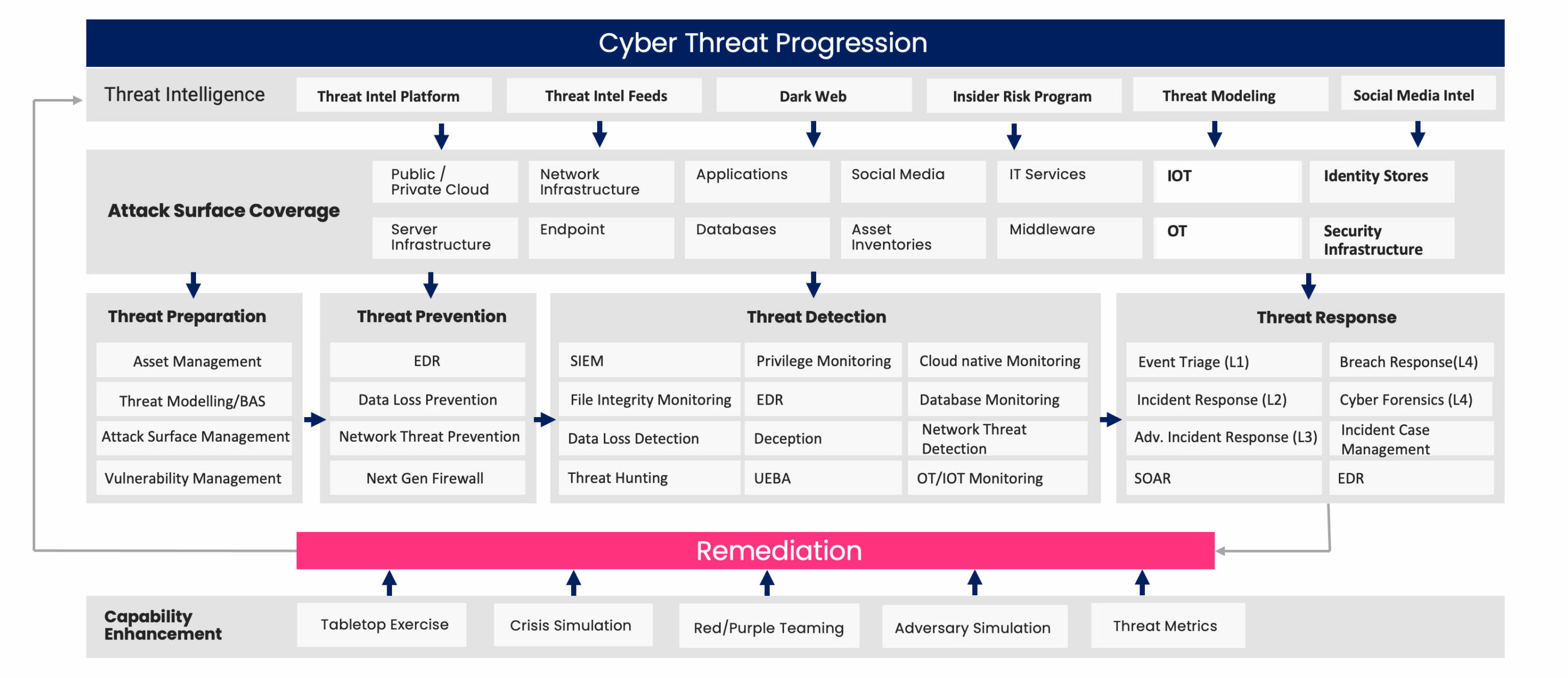
Predictive & Integrated Continuous Threat Exposure Management (ICTEM) framework
Dreamer People offers a proactive cybersecurity strategy that combines Predictive & Integrated Continuous Threat Exposure and Attack Surface Management (ICTEM) framework.
Through Predictive Threat Analysis, we enhance visibility into an enterprise’s security by using advanced AI/ML capabilities in real-time. This involves scrutinizing traffic, endpoints, and lateral movement to identify and mitigate security threats promptly.
Complementing this, our ICTEM framework takes a holistic approach by combining various strategies, technologies, and practices. Services include real-time threat intelligence, digital exposure monitoring, web monitoring, UEBA, threat hunting, and red/blue teaming. This active management ensures a robust cybersecurity posture.
Zero Touch Access Management
At Dreamer People we understand the importance of access governance and the complexity of deploying a mature Identity lifecycle management solution. Cumulative addition of access within an organization leads to an increased threat, that continues to be addressed through manual user access management solutions leading to productivity loss and compliance adherence.
Our approach is to understand the current process being followed and then introduce Robotic Process Automation (RPA) solutions to minimize the manual efforts and increase productivity to meet compliance objectives. Zero Touch User Access Management solution enables organizations to mature their Identity Governance journey in a phased manner to minimize risk exposure.