Threat Analytics
At Dreamer People, we recognize Threat Analytics as a pivotal element in safeguarding industrial control systems. This approach is integral, encompassing technology, procedural methodologies, and comprehensive personnel training. In response to the evolving threat landscape, continual improvement and collaboration between IT and OT security teams is imperative to uphold a resilient and secure operational environment.
Our Threat Analytics approach revolves around gaining comprehensive visibility into Network Traffic, Logs, and Events originating from critical systems such as Programmable Logic Controllers (PLCs) and SCADA systems. This approach provides deep insights into system behavior. We employ AI/ML techniques for threat detection, ensuring a proactive defense mechanism against emerging cyber threats.
IT/OT Convergence
IT/OT convergence refers to the growing integration of Operational Technology (OT) networks with Information Technology (IT) networks. Our experts recognize the transformative power of this convergence, particularly with the widespread adoption of the Internet of Things (IoT). This integration brings substantial benefits to industrial companies, fostering digitized processes and encouraging cross-organizational collaboration within the ecosystem.
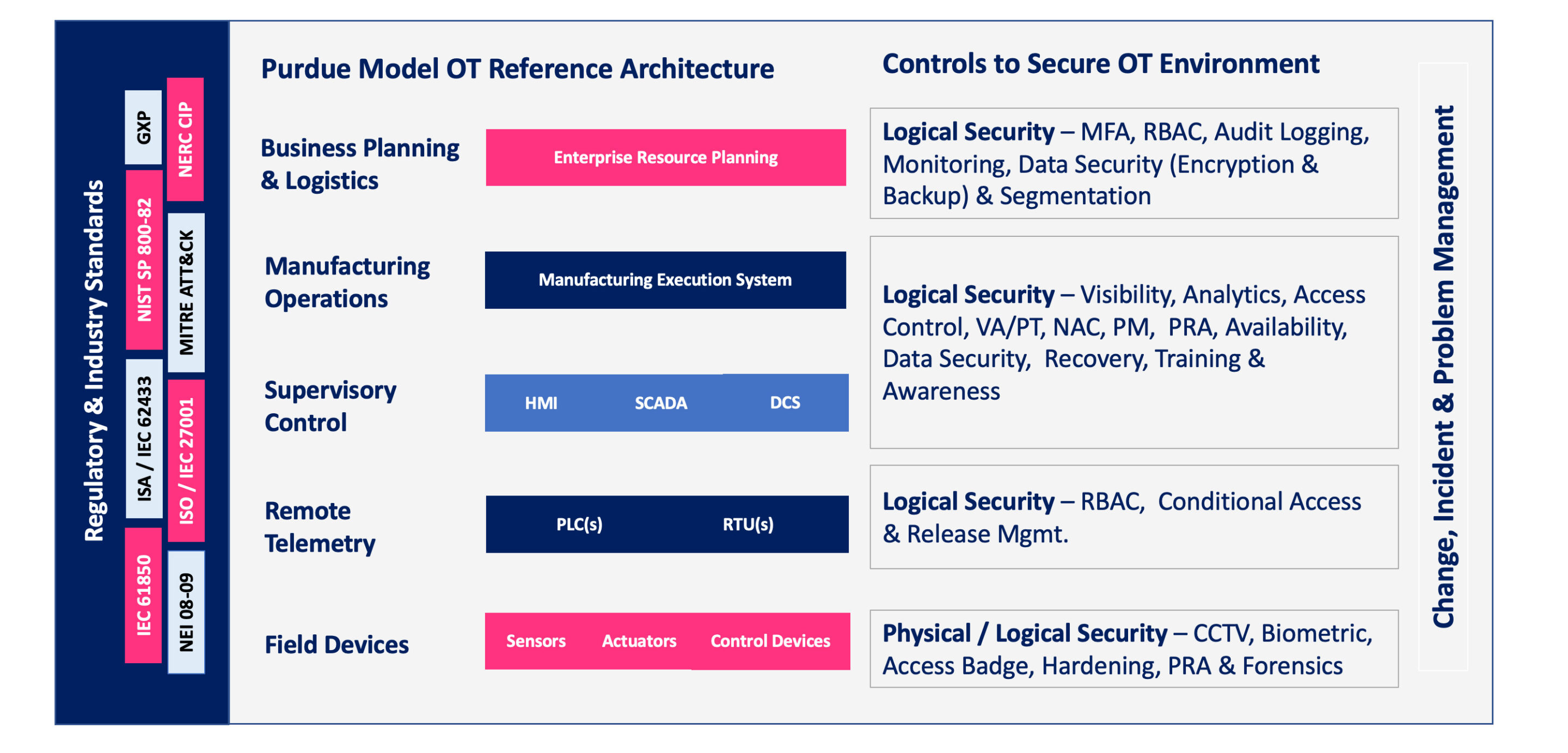
Yet, the melding of IT and OT networks expands the potential for cyber threats. Recognizing this, at Dreamer People, we specialize in IT/OT Security Convergence. Our focus is on fortifying systems and plants against cyber threats using industry best practices and frameworks.
Zero Trust for OT Security
Dreamer People advocates for a zero-trust model to safeguard OT environments from internal and external security threats amid the accelerated pace of IT/OT convergence. Our Zero Trust approach in OT is anchored in People, Process, and Technology.
People: Conduct periodic awareness campaigns to educate users about the risks of IT/OT convergence. Train them on leveraging zero-trust solutions for enhanced organizational security.
Process: Establish robust operational processes promoting best practices like Segregation of Duties (SoD), Maker & Checker, Continuous Security Monitoring, Privileged Access Management, and Secure Remote Access.
Technology: Evaluate zero-trust security solutions for OT environments from industry-leading OEMs. These solutions seamlessly address use cases across both IT and OT environments.